CVE-2018-18955 漏洞涉及到 User 命名空间中的嵌套用户命名空间,用户命名空间中针对 uid(用户ID)和 gid(用户组ID)的 ID 映射机制保证了进程拥有的权限不会逾越其父命名空间的范畴。该漏洞利用创建用户命名空间的子命名空间时损坏的 ID 映射实现提权。
漏洞分析 https://www.freebuf.com/vuls/197122.html
https://www.cnblogs.com/likaiming/p/10816529.html
影响范围 Linux kernel 4.15.x through 4.19.x before 4.19.2
4.19.2 之前的 Linux 内核 4.15.x 到 4.19.x 中
exp https://github.com/bcoles/kernel-exploits/tree/master/CVE-2018-18955
https://github.com/SecWiki/linux-kernel-exploits/tree/master/2018/CVE-2018-18955
漏洞复现 安装uidmap 1 sudo apt-get install uidmap
编译执行 exploit.cron.sh >> root
会在cron日志留下记录
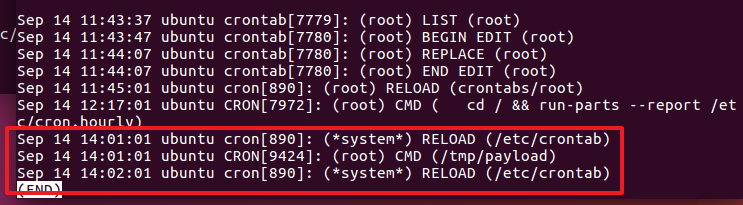
1 2 3 Sep 14 14:01:01 ubuntu cron[890]: (*system*) RELOAD (/etc/crontab) Sep 14 14:01:01 ubuntu CRON[9424]: (root) CMD (/tmp/payload) Sep 14 14:02:01 ubuntu cron[890]: (*system*) RELOAD (/etc/crontab)
auth日志
1 2 Sep 14 14:01:01 ubuntu CRON[9423]: pam_unix(cron:session): session opened for user root by (uid=0) Sep 14 14:01:01 ubuntu CRON[9423]: pam_unix(cron:session): session closed for user root
警告 这个只能够提权一次,第二次提权就如下图所示
exploit.dbus.sh >> root
subuid_shell >>nobody提权到nobody权限
权限为:uid=65534(nobody) gid=65534(nogroup) groups=65534(nogroup)
但是这个nobody好像权限很大。
Linux namespace之:user namespace
exploit.ldpreload.sh >> root (优先)
exploit.polkit.sh >> root 需要 owner的密码
日志,第一次用test账号密码 是FAILED 第二次owner账号密码successfully
修复 https://git.kernel.org/pub/scm/linux/kernel/git/torvalds/linux.git/commit/?id=d2f007dbe7e4c9583eea6eb04d60001e85c6f1bd
日志特征 /var/log/audit/audit.log1 2 3 4 5 6 7 8 9 10 11 type=USER_CMD msg=audit(1631519751.428:28): pid=9625 uid=0 auid=4294967295 ses=4294967295 msg='cwd="/var/log/audit" cmd=6170742D67657420696E7374616C6C207569646D6170 terminal=pts/1 res=success' type=CRED_REFR msg=audit(1631519751.428:29): pid=9625 uid=0 auid=4294967295 ses=4294967295 msg='op=PAM:setcred acct="root" exe="/usr/bin/sudo" hostname=? addr=? terminal=/dev/pts/1 res=success' type=USER_START msg=audit(1631519751.428:30): pid=9625 uid=0 auid=4294967295 ses=4294967295 msg='op=PAM:session_open acct="root" exe="/usr/bin/sudo" hostname=? addr=? terminal=/dev/pts/1 res=success' type=USER_END msg=audit(1631519756.544:31): pid=9625 uid=0 auid=4294967295 ses=4294967295 msg='op=PAM:session_close acct="root" exe="/usr/bin/sudo" hostname=? addr=? terminal=/dev/pts/1 res=success' type=CRED_DISP msg=audit(1631519756.544:32): pid=9625 uid=0 auid=4294967295 ses=4294967295 msg='op=PAM:setcred acct="root" exe="/usr/bin/sudo" hostname=? addr=? terminal=/dev/pts/1 res=success' type=USER_ACCT msg=audit(1631519821.588:33): pid=10062 uid=0 auid=4294967295 ses=4294967295 msg='op=PAM:accounting acct="root" exe="/usr/sbin/cron" hostname=? addr=? terminal=cron res=success' type=CRED_ACQ msg=audit(1631519821.588:34): pid=10062 uid=0 auid=4294967295 ses=4294967295 msg='op=PAM:setcred acct="root" exe="/usr/sbin/cron" hostname=? addr=? terminal=cron res=success' type=LOGIN msg=audit(1631519821.588:35): pid=10062 uid=0 old-auid=4294967295 auid=0 tty=(none) old-ses=4294967295 ses=4 res=1 type=USER_START msg=audit(1631519821.588:36): pid=10062 uid=0 auid=0 ses=4 msg='op=PAM:session_open acct="root" exe="/usr/sbin/cron" hostname=? addr=? terminal=cron res=success' type=CRED_DISP msg=audit(1631519821.604:37): pid=10062 uid=0 auid=0 ses=4 msg='op=PAM:setcred acct="root" exe="/usr/sbin/cron" hostname=? addr=? terminal=cron res=success' type=USER_END msg=audit(1631519821.604:38): pid=10062 uid=0 auid=0 ses=4 msg='op=PAM:session_close acct="root" exe="/usr/sbin/cron" hostname=? addr=? terminal=cron res=success'
auth.log 1 2 3 4 5 Sep 13 00:57:01 ubuntu CRON[10062]: pam_unix(cron:session): session opened for user root by (uid=0) Sep 13 00:57:01 ubuntu CRON[10062]: pam_unix(cron:session): session closed for user root Sep 13 00:58:51 ubuntu pkexec: pam_unix(polkit-1:session): session opened for user root by (uid=1000) Sep 13 00:58:51 ubuntu pkexec: pam_systemd(polkit-1:session): Cannot create session: Already running in a session Sep 13 00:58:51 ubuntu pkexec[10096]: owner: Executing command [USER=root] [TTY=unknown] [CWD=/home/owner] [COMMAND=/usr/lib/update-notifier/package-system-locked]